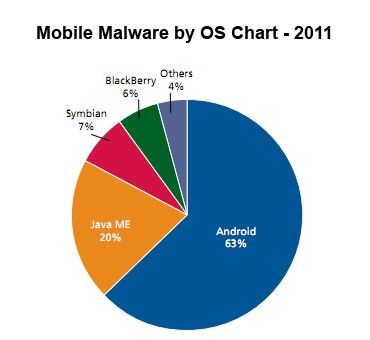
As many as 96.5% of mobile infections attack Android system
10 rules for safe use of smartphones and tablets. FortiGuard Labs expert advises how to easily protect your smartphone and tablet from cybercriminals’ attacks and mobile viruses.
With the consistent increase in computing power and the development of new technologies (such as 4G), the capabilities of smartphones and tablets are getting better every month. With the proliferation of devices and the drop in their prices due to lower production costs, we can expect a further increase in the number of smartphone and tablet users, and thus also in the number of units sold. Forecasts predict that users will increasingly use mobile devices at the expense of laptops and desktop PCs. The presence of this trend is confirmed by the fact that in 2021 already 15% of global Internet traffic came from mobile devices.
It is estimated that by 2017 there will be a thirteenfold increase in the popularity of such gadgets. Of course, cybercriminals have also recognized this trend and are actively operating in the new market. Faced with this threat, users need to be especially careful and vigilant when using their mobile devices.
Below we discuss 10 proven ways to ensure your mobile security.
1. Don’t download apps from unofficial sources
Thanks to the existence of app stores – Apple App Store and Google Play Store – users can download applications from a central, constantly monitored source. Restricting the search for new apps to these stores greatly reduces the risk of downloading and installing malware (except in cases where someone somehow bypasses the verification performed by their operators). Android’s default setting, allowing installation of applications from other sources, should be disabled.
This way, the phone will display a warning every time the user tries to install an application coming from an unofficial store.
2. Check the level of permissions that apps request
In the case of Android, currently the most frequently attacked mobile operating system in the world, one should always carefully review the permissions requested by the app. The user must decide whether the scope of required permissions corresponds to the theoretical operation of the application. This is a very simple, but often surprisingly effective way to identify malware.
For example, a calculator should not require us to access a camera or GPS system. Requiring permissions completely incompatible with the purpose of the application should light an alarm light in the user’s mind. Aware of the risks to their phone, the user will opt out of installing such an application.
3. Watch what links you click on
As with personal computers, it is always imperative to be careful what you click on. A common way used by cybercriminals is to send text messages containing links to Web pages, starting the download of a malicious application. If an inattentive user uses such a link, he may infect his phone without realizing it. It’s also important to remember that on small smartphone screens, checking the URL thoroughly can be problematic due to limited space in the address bar.
The matter is further complicated by the increasing use of URL shortening services. The surest way to avoid getting your phone infected in this way is to simply Refrain from using links from unknown or untrusted sources. Importantly, it is a good idea to check the address of the visited site even if the link comes from a trusted source.
4. Watch out for unsecured and public wireless networks
Be very careful when using unsecured and public wireless networks. Anyone watching traffic on such a network will see all unencrypted data – including usernames and passwords – transmitted in open text. The best way to avoid an attack of this kind is to Visiting only sites and services that encrypt traffic using HTTPS for valid purposes.
The protocol encrypts all data sent between the smartphone and the destination, so a web peeper won’t be able to read it.
5. Block unwanted ads
Many websites and applications dedicated to mobile devices derive a lot of profit from the so called “mobile web”. AdKit packages. They collect information about the user in order to then display ads better tailored to the user’s interests. Although the very idea behind AdKit packages is not to harm the user, the information they collect can violate privacy.
The simplest solution to this problem is to install ad-blocking software, such as AdBlock. This software blocks all traffic related to ads, thus protecting sensitive user data.
6. Remember to log out of websites
An increasing proportion of Web site traffic is generated by mobile devices. So it’s no surprise that cybercriminals are looking to capitalize on this trend with their. We have already witnessed several attacks this year that exploit security vulnerabilities in browsers installed on cell phones.
These applications are generally less secure than their PC counterparts. That’s why, in addition to keeping a close eye on the sites you visit, it’s always a good idea to log out of a Web site when you’re done using it. This will result in the deletion of login data (stored e.g. in the form of cookies), reducing the user’s vulnerability to attacks of this kind.
7. Install an antivirus
Some antivirus software manufacturers offer free antivirus programs for Android phones. These are automated solutions that will quite effectively protect the device from viruses. However, it is imperative to be wary of fake antivirus, most often ransomware.
So before downloading a mobile antivirus, make sure (e.g. reading online forums or product reviews), whether it is a malicious worm extorting money from us in exchange for the ability to unlock the services we need (which it has previously blocked itself).
8. Be aware of attacks carried out through USB ports
Although this is a fairly rare form of attack, it is important to know about it and beware of it. It involves sending malware from an infected PC when a phone is connected to it via a USB cable. Even if we just wanted to charge the battery, we can fall victim to a cyber attack.
A good and inexpensive way to protect yourself from this threat is to use “USB condoms.”. USB Condoms, http://www.usbcondoms.com/), which prevent data from being read from and written to the phone. This solution guarantees that the USB connection will only be used to charge the battery.
9. Keep your operating system up to date
It is a good idea to regularly update the operating system. In addition to improving operations and gaining access to new features, the user also increases the security level of his smartphone in this way.